In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.
In this article, we'll look at how to grab the password hashes from a Linux system and crack the hashes using probably the most widely used password cracking tool out there, John the Ripper.
Let's boot up BackTrack and get hacking!
Where Linux Passwords Are Stored
Linux passwords are stored in the /etc/passwd file in cleartext in older systems and in /etc/shadow file in hash form on newer systems. We should expect that the passwords on anything other than old legacy systems to be stored in /etc/shadow
Step 1: Create Some User Accounts
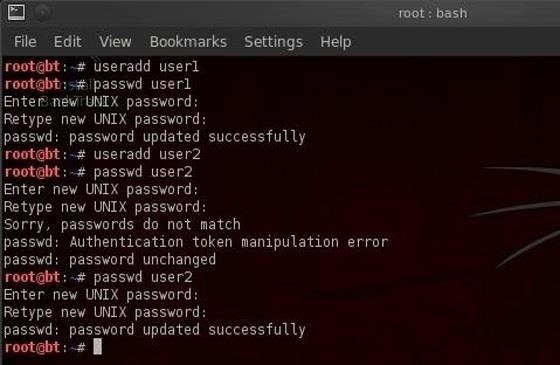
Since our BackTrack system probably doesn't have many users on it other than our root account, let's go ahead and create a couple more accounts.
Let's create user1 with password "flower" and user2 with a password of "hacker".
I've purposely chosen dictionary words as the complexity of the password is inversely related to the time necessary to crack it. One of the nice features of John the Ripper is that it will try to use a dictionary attack first. If that fails, it will try a hybrid attack. And only if that fails will it attempt a brute-force attack, which is the most time consuming.
Step 2: Open John the Ripper
Now that we have a couple of regular users in our system with simple passwords, we now need to open John the Ripper. John the Ripper is a simple, but powerful password cracker without a GUI (this helps to make it faster as GUIs consume resources).
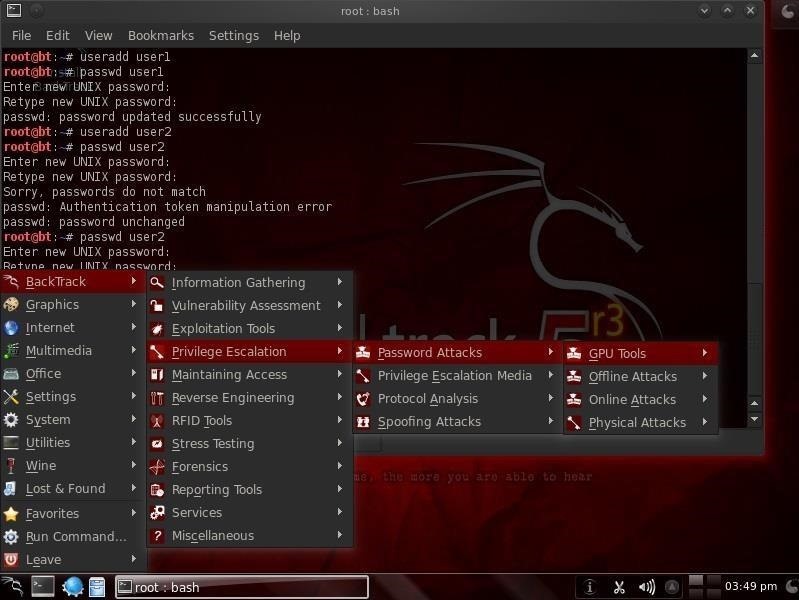
We can access it from BackTrack by going to the BackTrack button on the bottom left, then Backtrack, Privilege Escalation, Password Attacks, Offline Attacks, and finally select John the Ripper from the multiple password cracking tools available.
If you selected the correct menu item, it will open a terminal that looks like this.
By the way, feel free to close our previous terminal as we're finished with it.
Step 3: Test John the Ripper
At the prompt, type:
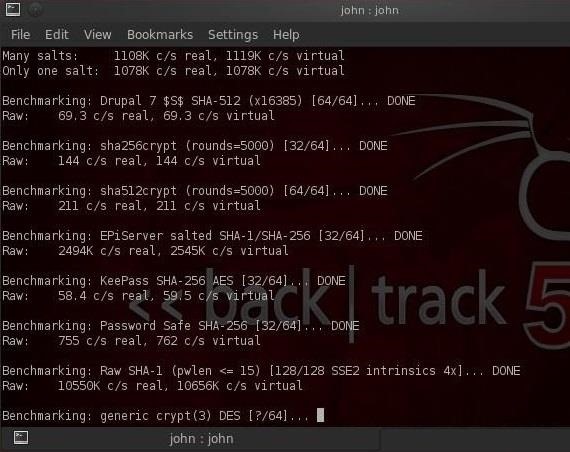
- bt > john -test
This command will send John the Ripper through a variety of benchmark tests to estimate how long it will take to break the passwords on your system. Your terminal will look something like this.
Now that John has estimated how long each of the encryption schemes will take to crack, let's put him to work on cracking our passwords.
Step 4: Copy the Password Files to Our Current Directory
Linux stores its passwords in /etc/shadow, so what we want to do is copy this file to our current directory along with the /etc/passwd file, then "unshadow" them and store them in file we'll call passwords. So, let's type both:
- bt > cp /etc/shadow ./
- bt > cp /etc/passwd ./
In Linux, the cp command means copy and the ./ represents our current directory. So this command says, copy the contents of /etc/shadow to my current directory. We do the same for the /etc/passwd file.
Step 5: Unshadow
Next we need to combine the information in the /etc/shadow and the /etc/passwd files, so that John can do its magic.
- bt > ./unshadow passwd shadow > passwords
Step 6: Crack!
Now that we have unshadowed the critical files, we can simply let John run on our password file.
- bt > john passwords
John the Ripper will proceed to attempt to crack your passwords. As you can see, it cracked all three of ours in a matter of seconds! Of course, more complex passwords will take significantly more time, but all we need is just one user with a simple password and we have access to the account in seconds.
It's also important to note that any password cracker is only as good as its word list. For more complex or hybrid passwords, you probably want to use a password list containing far more passwords, including hybrid passwords such "p@$$w0rd" that combine special characters into words.