Todays As per as we use our pen-drives and other Hard drive in our
Pc/Laptops.We face some shortcuts which harm our files. So The questions arises That from where that shortcuts Comes? And after all The main question that we dont know that How To Remove Shortcut Virus From Pendrives or PC.
What Is Shortcut Virus ?
A shortcut virus is a virus (a malware) that hides your original files inside shortcuts.The way it hides the file remains unknown though the effect is quite visible. The original files are there in the drive itself, but in such a position that you can’t recognize it nor take it out. Shortcut Virus Sometimes delete your important data.
Initially, it doesn’t harms your files but later on, it may make them corrupt or even delete all the files; depends on the type of shortcut virus.
F
Remove Shortcut Virus From PC or Pendrive
#Method-1
#Remove Shortcut Virus From Pendrive/PC Using CMD/Command Prompt.
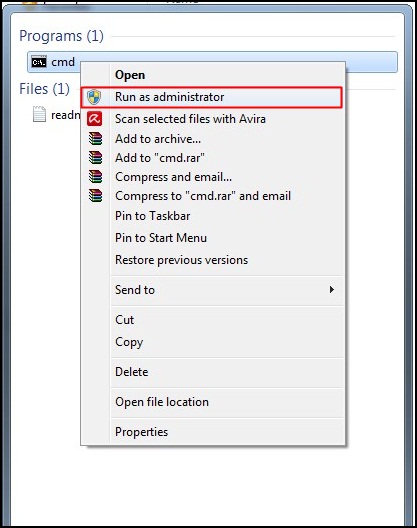
1.Go to Start Type "Run" > Type "CMD"> Open Command Prompt in Administrative Mode.
2.A black Color of window is open infront of you.
3.Type in Command prompt : attrib -h -r -s /s /d <Your USB drive letter>:\*.*(See <Your USB drive letter> from My computer and then type it For ex, if your drive letter is “D” then the command is like: ” attrib -h -r -s /s /d D:\*.* “)
To know about this command Type ” attrib /? ” In CMD Window.you can know more about it.
Lets Take An Example :- If My removable disk drive (pendrive) has a Latter of "F" then i have to use USB Drive Letter "F".
By this simple method you can Remove shortcuts from your pendrives/pc.
#Problem Facing- Remove Shortcut Virus Using command prompt/CMD
While you are using this attribute your System files may or maynot be Remove some virus from FAT32 & NTFS.
#Method-2
Shortcut Virus Remover : Remove Shortcut Virus Using Shortcut Virus Removers.
So Here We have many software which helps you to remove shortcut virus from pendrive/PC/SD cards. But here Mukeshtricks4u.com Gives you best Shortcut Virus Remover Software.
Rkill Virus Remover
Rkill Latest Software To Remove Shortcut Virus From Pendrive/PC.
RKill is a Shortcut virus Remover software designed to terminate malware processes that blocks or prevents your security software (Antivirus, Anti-malware and etc.) from running. In order that, you can start using security software again and be able to clean Your Pendrive from virus.
NOTE- RKill is not an Antivirus or malware Removal Tool, it has no power to remove malware. But it stops malicious or malware processes to help Antivirus and Anti-malware remove stubborn malware.i suggest You all to use Rkill only for removing of Shortcut virus from pendrives/PC
Q. How to fix Security warning that RKills is infected & Harmful?
Relax Guyz If Dont Worry about it, Beeping Computer (software Computerauthor) is known to have a very good reputation against malware. It is a false alarm or a bogus alert caused by malware to shield itself,
If you are using Comodo, Kaspersky and Trend Micro you may receive a false positives. However, be rest assured that RKill is clean and won’t hurt your system. So, just ignore those false positives. The author already submitted the tool to Antivirus vendors mentioned above so that they can whitelist it.
Q. How to do whitelist of some files that RKill Wont Scan?
In my experience, I don’t think this is necessary. It is accurate enough, it doesn’t kill legitimate processes. However, in case this is an issue for you — in command prompt type the following rkill -w c:usersdataprogram filesfile.exe.
Download RKill Virus Remover Software Latest -
Download Rkill Free
 Over two weeks after the shutdown of Kickass Torrents and arrest of its admin in Poland, the world's biggest BitTorrent meta-search engine Torrentz.eu has apparently shut down its operation.
Over two weeks after the shutdown of Kickass Torrents and arrest of its admin in Poland, the world's biggest BitTorrent meta-search engine Torrentz.eu has apparently shut down its operation.










 I have been a Pokemon Go player for over a month now, and I did not believe such website exist, let alone, a tool like this. I was so skeptical at first just like any of you here, but something pushed me to try this tool. And now, I am very thankful of that because, I can fully enjoy and grasp the concept of the game, more than any of you here.. Now, I don't have to spend a lot of days waiting or finding or leveling or farming money in the game, who would want to do that? I know most of you are sick and tired of this "Free-to-Play" scheme, where you play the game for free yet you will face the reality of having hindered to play it the way you want it to be because you are required to spend real cash..
I have been a Pokemon Go player for over a month now, and I did not believe such website exist, let alone, a tool like this. I was so skeptical at first just like any of you here, but something pushed me to try this tool. And now, I am very thankful of that because, I can fully enjoy and grasp the concept of the game, more than any of you here.. Now, I don't have to spend a lot of days waiting or finding or leveling or farming money in the game, who would want to do that? I know most of you are sick and tired of this "Free-to-Play" scheme, where you play the game for free yet you will face the reality of having hindered to play it the way you want it to be because you are required to spend real cash..







