Hack Facebook Account By Cookie Stealing And Session Hijacking Wiith Wireshark
Wireshark Software to capture cookies:
Wireshark is the best free packet sniffer software available today. Actually, it was developed for making a network secure. But, the same software is now used by hackers to test for vulnerability and security loopholes in the network and to attack the network accordingly. Cookie stealing being one of the types of hacks implemented using this Wireshark software.
Requirements:
Prerequisites: Download and install all above programs. To add “Add n Edit” to your browser just open firefox, go to tools, then click add-ons. you can drag and drop the program from wherever you saved it into the little box that popped up and install it from there.
Below, I have listed steps on how to capture Facebook and other accounts cookies. This will help you to know how Wireshark and Cain-Abel can be used to sniff packets and capture cookies.
First: Gain acess to the Network. Open networks or your own network would be easy but if you have a specific slave you want you should be able to gain acess using Backtrack.
Tip: use reaver to exploit WPS for WPA/WPA2 encryptions, WEPs are easy to crack given time and OPN means there is no password.
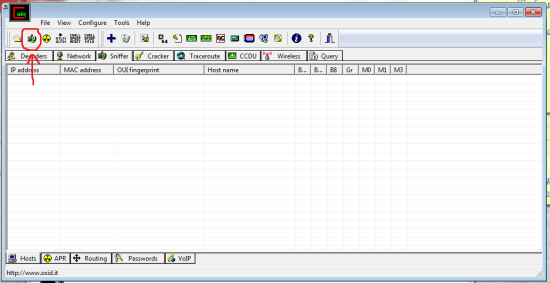
Second: Right click Cain and choose ‘run as administrator.’ on the top bar go to ‘configure’ and be sure to select your wireless card/adapter. now click where it says ‘Sniffer’ then this litte button towards the top left:
Next click any empty white box then the blue “+” symbol near the button you pressed just before. choose okay
should look like this:
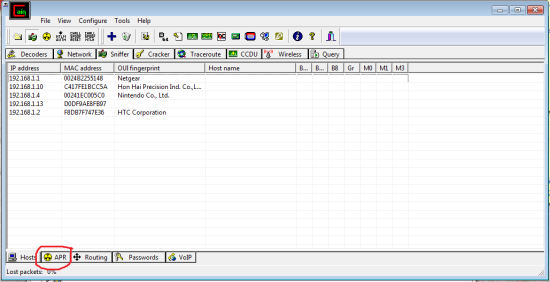
These are all the devices it was able to detect.
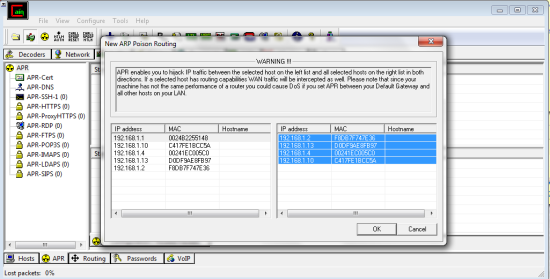
Now we go to APR on the bottom bar. Once again click any empty white box then the blue cross. It’s easiest to just go one by one and choose all possibilities.
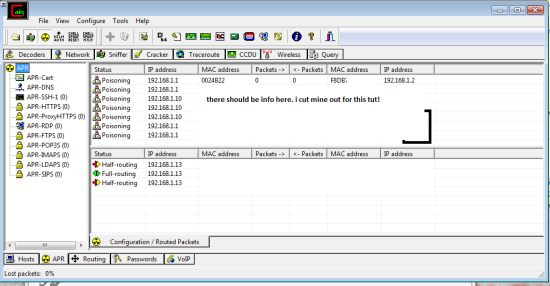
Now we have to poison them so we choose the little yellow hazard symbol towards the top left. should now look like this:
we are done here, just minimize Cain for now.
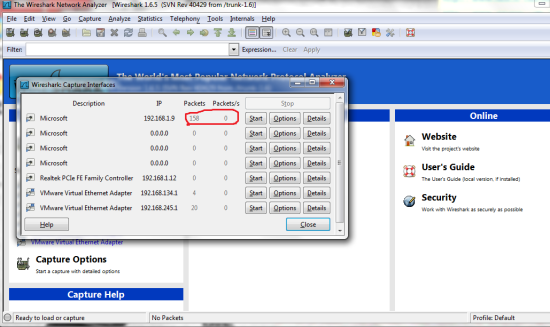
Third: Run wireshark as administrator. On the top bar choose ‘Capture’ then ‘Interfaces.’ Here you will have to choose your interface that is connected to the Network we are sniffing from. if you wait a few seconds you might see some traffic being collected as seen in my photo, just choose that interface b/c thats most likely it.
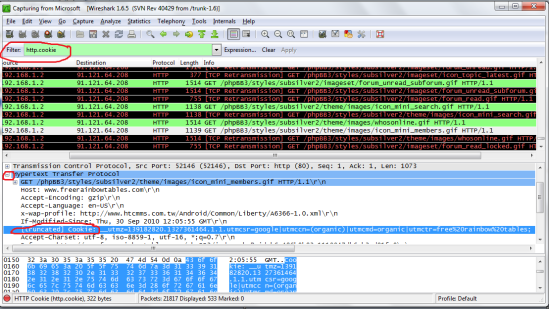
Wireshark will list and color-code all the traffic it sees for you. To make this simpler we can use the filter to only see the traffic we want, Type “http.cookie” in the filter. (Something to consider is to just filter to “http” and scroll through the entries looking for ones that start with the word “POST” this means that information was submitted to the webpage noted such as a username and a password! so if you see this just look through the details and you should see the info you want, most passwords will be hashed but use this site to decript them:http://www.md5decrypter.co.uk/ )
Here is an image:
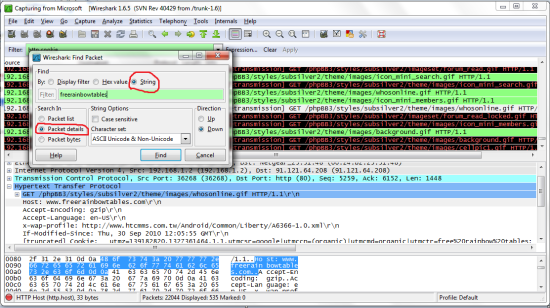
You can either look through this information manually or use the search function to find what you want. In my case i want to hijack the session of a user on the forumfreerainbowtables.com so i will use the search function (press Ctrl+F, or go to edit -> search) and type in the information i know for sure will be in the entry. if your hijacking someones facebook put ‘facebook’ there. Most of the time to be safe i do not use the first entry i see b/c this will only work if the person is auto logged in, so just go down a few more until you see one you think will work (just use common sense).
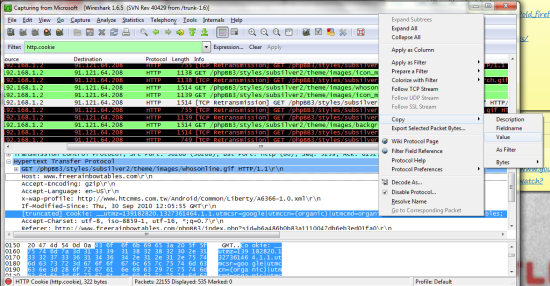
What we need are the cookies. Here are what mine look like and how to get there. With practice you will be able to tell which cookies are used for logins and be able to limit failed attempts.
Copy the cookies as value and save them into a notepad (shown in pic above). I would suggest to seperate everywhere you see a “;” bc this suggests that is the begining of the next entry. The text to the left of the = is the name of the cookie and the text to the right is its value.
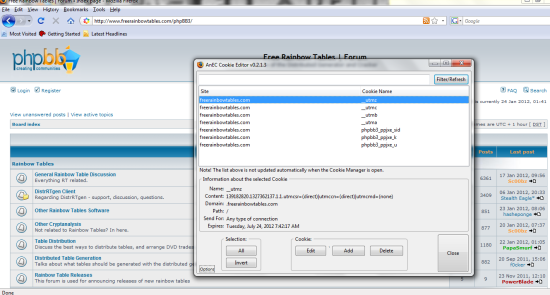
Final: Open up your firefox browser with Add n Edit enabled. You can get to your add ons by going to tools and they should all be listed in the drop down tab. First go to the website you are hijjacking the session from then open your cookie editor. Should look something like this:
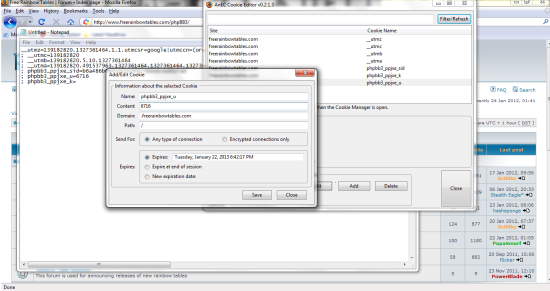
The last thing to do is to change your cookies to match the ones you captured. If the cookies given to you by the site expire (like the ones in my picture do) you will have to delete them and add all the ones we captured earlier in. if they do not expire you can just edit them. Bottom line is all the cookies must match the cookies you captures in the earlier steps EXACTLY! Make sure you do not add any extras and that you did not miss anything. Also all fields must be filled in (Path and Domain as well as Name and Value). My path is “/” and my domain is “.freerainbowtables.com”
mine looks like this:
You are now done, Just close the cookie editor and reload the webpage. If done correctly with the correct cookies you should be logged in as the user you attacked!












![[WhatsApp Hacks] Crash Your Friend’s WhatsApp [WhatsApp Hacks] Crash Your Friend’s WhatsApp](https://techviral.com/wp-content/uploads/2014/12/Crash-Your-Friend%E2%80%99s-WhatsApp1.jpg)
